'Mantis' tries to solve the LLM prompt injection attack problem | How to protect yourself from Government Surveillance
#167 - A counterattack based solution that looks promising | An increased fear of government surveillance and ways to protect yourself
Can the LLM prompt injection attack problem be solved?
Finding unique solutions to the ‘hard’ problem of LLM security
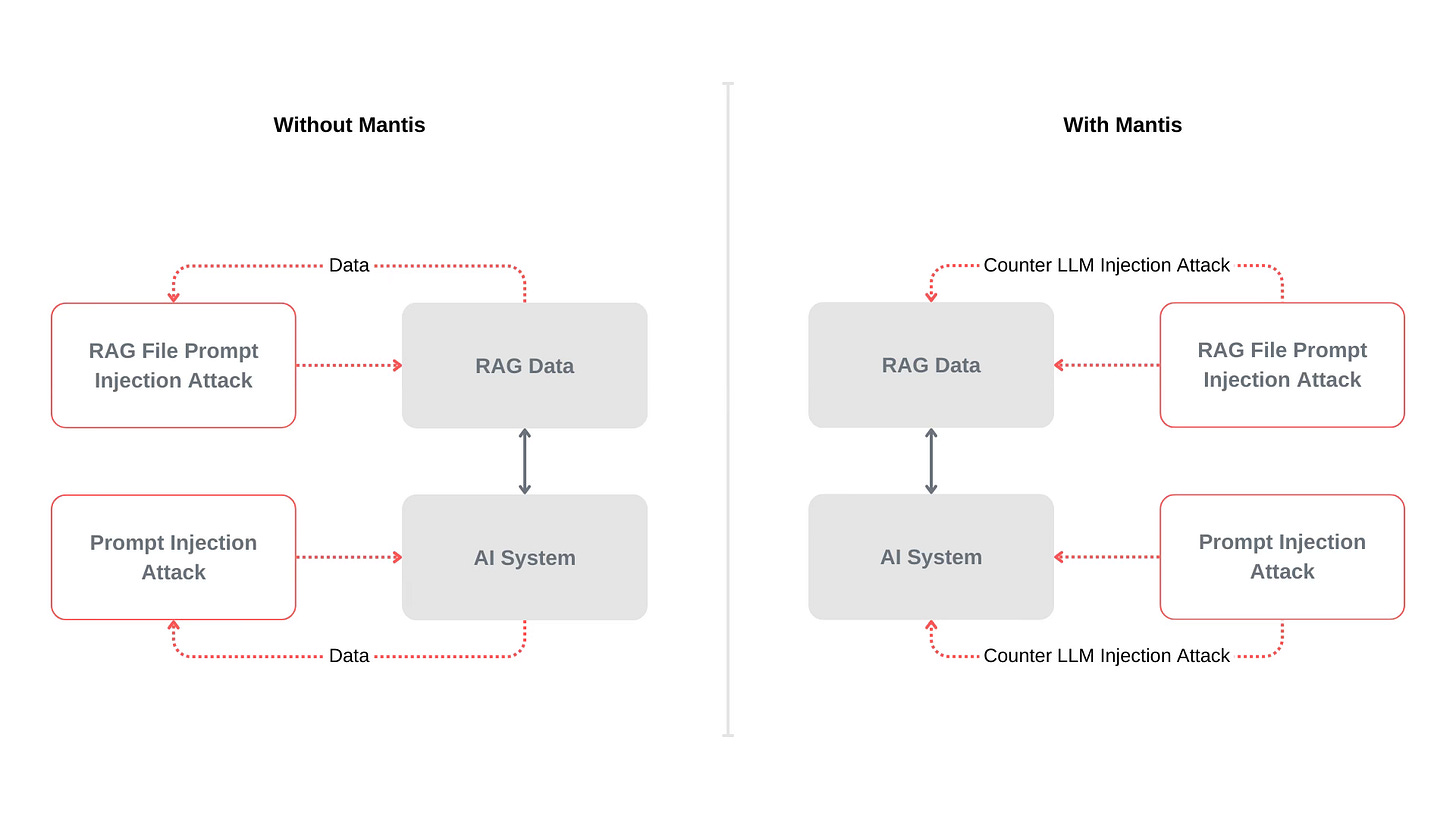
Prompt injection attacks are the new attack vectors. You can inject prompts into LLMs in two ways
directly chatting with their interface or API
injecting malicious files into a RAG ecosystem (Retrieval Augmented Generator)
In either case, this is a hard problem to solve.
Just like the regularly used door is a weak link in your fortress, a communication interface (web or API) is a weak link in your LLM interface. You are tasked with allowing all the genuine people through, but not allowing the malicious elements. The malicious elements are generally disguised as genuine people.
Mantis, an experimental solution, tries a unique approach to LLM security. If an LLM is attacking another LLM, as is the case with most automated prompt injection attack tools, Mantis returns a malicious prompt back. Something like this:
Since the attacking LLM tries to interpret data that the victim LLM is sending, it is more susceptible to a counter attack.
Take Action:
If you are red teamer and use LLMs by integrating them with your attack tools (like Kali with ChatGPT), you should consider the scenario of a counter attack.
If you are a blue teamer, evaluate the feasibility of using tools like Mantis for protecting your LLM. Read the paper here.
If you are an AI developer, think of building a counter attack system right into the interface logic. This could be a smart way to solve the hard problem of prompt injection.
How to protect yourself (at least partially) from government surveillance
Governments were always surveilling, it’s probably going to be more open now
It’s too low hanging a fruit for any government to not be tempted by. Surveillance is a part of the digital economy and that will not change with any government coming to power. And once a surveillance ecosystem is setup, it continues. It’s very hard to reverse it.
However, with the imminent change of guard at the White House, there are fears of increased surveillance.
Wired has released a guide to protect your privacy online. It’s always good to protect your privacy online.
The article delves into the following areas:
Encrypted Communication
Encrypted Devices
Cloud storage privacy
Online anonymity
Location data privacy
Financial privacy
An interesting side on burner phones
Take Action:
This is at an individual level, not the company.
Go through the guide, implement systems that you think will help your case.
Use your superpower for good. Assist people with lesser technical skills to protect their privacy better.