NPM Hack - the biggest of the year?
#203 - More than 180 NPM packages hit by a self replicating worm

What is the Node Package Manager (NPM)?
NPM or the Node Package Manager is a library of software packages that are available to software developers. These packages are brought into their code by developers and used for performing specific tasks. Do you want to make your output in the terminal colorful? Run
npm install chalkand you have a nifty little utility to do that.
There are various package managers for various programming languages. I have written about the Python Package Index (PyPI) attacks multiple times over the years.
Why is a package manager targeted?
Package managers are seamlessly integrated into a developers workflow. For example, if you are a data scientist and want to start a new project, you start with installing and importing the most popular libraries used for data science:
import pandas as pd
import numpy as np
import matplotlib.pyplot as plt
import seaborn as snsYour first actions are importing popular packages. No point in re-learning how to make the wheel, right?
These packages are open source and maintained by individual developers or a community of developers. Popular packages can have millions of downloads.
If an attacker can get their malicious code into one of these packages, they have access to millions of systems. This makes any package manager library an attractive target.
What happened with NPM?
It does not begin very dramatically:
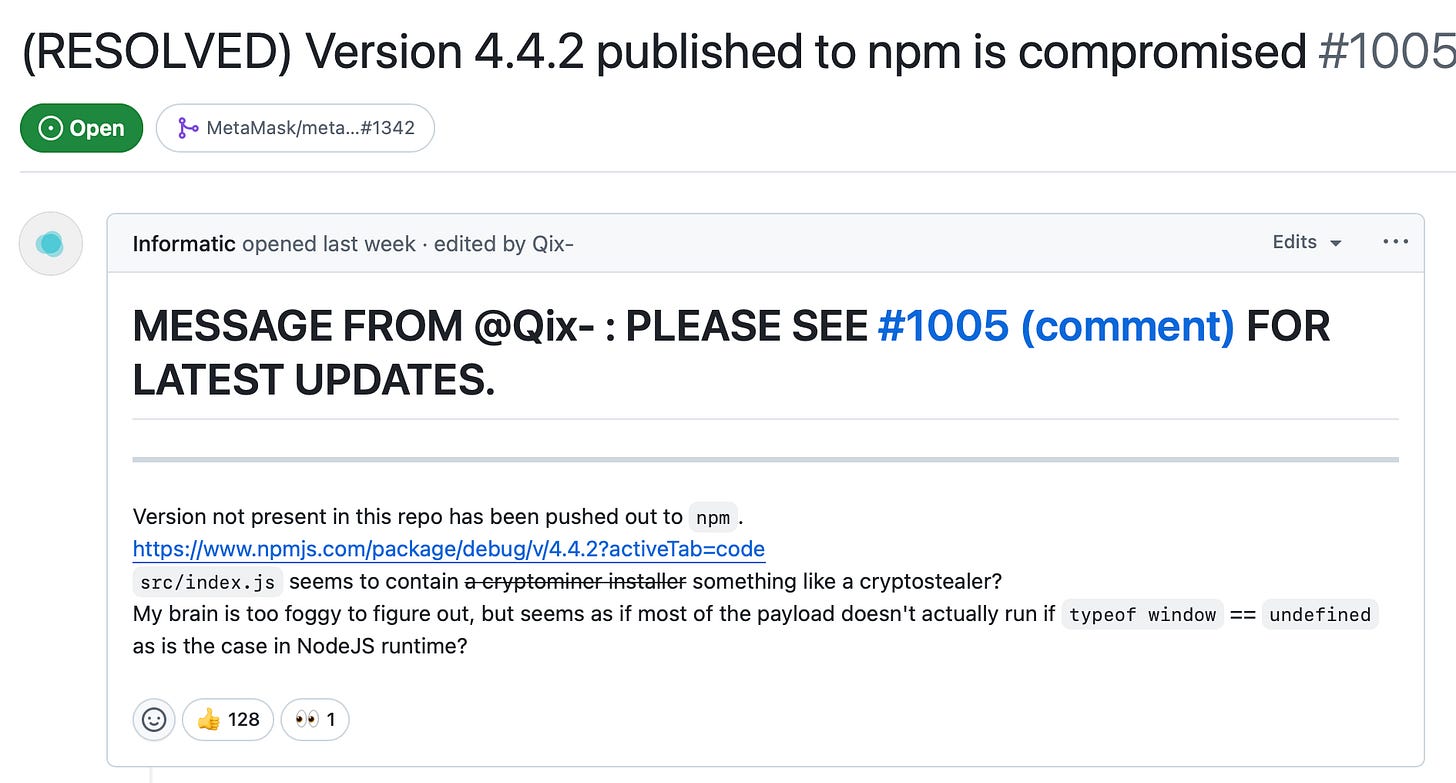
A maintainer of some of the most popular packages on NPM received a phishing mail. The mail asked to verify the 2FA to NPM.
Link Clicked. Credentials Entered. Credential Compromised.
The attackers then changed the packages to include malicious crypto-miners (or crypto-stealers) - something to do with crypto. Qix - the maintainer realised this and proceeded to rectify the damage caused.
Shai-Hulud
The quick response from Qix was not the end of it. Many developers received similar phishing mails and got their credentials compromised. The attacker used the compromised accounts to run a library that looks for secrets like API keys. If they found any, they created a public repository titled ‘Shai-Hulud’ for that developer and posted the secret there. This has happened for 180+ NPM packages.
Take Action
CISOs 👩🏻💼: If your dev stack is node, then you have to do the following:
Look up your SBOM (You have an SBOM, don’t you) and identify packages that may have been compromised.
Update compromised packages to the latest versions. If the latest versions are unavailable, downgrade to known clean packages.
Check your corporate code base as well as each individual developers code account to see if a public Shai-Hulud repo has been created. This is a clear sign of using compromised NPM packages as well as some exposed secret in the code base
On any sign of compromise, change all API tokens or any secrets used