NIST’s updates its password guidelines
But there's more to the NIST 800-63 update than just passwords
NIST updated their guidelines for passwords in NIST 800-63B. While password guidelines being changed is an important update, the whole authentication and authorisation guideline has received an update.
This is the second draft, released for comments before the final release. Find the link to the documents here.
Why is it a big deal?
The NIST 800-63 series is about ‘Digital Identity' and ‘Access Management’. Most IDAM tools that you see will follow these guidelines. All the archaic rules that you have thrust upon users (or had them thrust upon you as a user) originate here.
Before we discuss passwords, here is a brief summary of the three documents:
NIST SP 800-63A - Identify Proofing Process
This document describes the whole process of identity proofing:
In 800-63A, the details for a ‘Credentials Service Provider’ or CSP, to validate a user’s digital identify. There are 3 identity levels. IAL1, IAL2 and IAL3 - each with increasing levels of scrutiny for validating the evidence provided by a user to identify himself/ herself in the digital world.
NIST SP 800-63B - Authentication
Once an identify is verified, the second part is authenticating the identity online. There are again 3 authentication assurance levels - AAL1, AAL2 and AAL3.
AAL1 requires only one authentication - could be a password or your biometrics or any other authenticator.
AAL2 requires 2FA - This is the standard level of authentication that we have come to expect in most applications
AAL3 requires keys and uses public key cryptography - This is the most advanced authentication level.
It is in this document that you will come across all the hullabaloo on the internet. There are some important and interesting updates here:
The following authentication types are permitted for AAL 1 (verbatim):
Password: A memorizable secret typically chosen by the subscriber
Look-up secret: A secret determined by the claimant by looking up a prompted value in a list held by the subscriber
Out-of-band device: A secret sent or received through a separate communication channel with the subscriber
Single-factor one-time password (OTP): A one-time secret obtained from a device or application held by the subscriber
Multi-factor OTP: A one-time secret obtained from a device or application held by the subscriber that requires activation by a second authentication factor
Single-factor cryptographic authentication: Proof of possession and control via an authentication protocol of a cryptographic key held by the subscriber.
Multi-Factor cryptographic authentication: Proof of possession and control via an authentication protocol of a cryptographic key held by the subscriber that requires activation by a second authentication factor
As you can see, quite a detailed list. And then there are more for AAL2 and AAL3.
When Password is chosen as a verifier, then there are 9 requirements:
Verifiers and CSPs SHALL require passwords to be a minimum of eight characters in length and SHOULD require passwords to be a minimum of 15 characters in length.
Verifiers and CSPs SHOULD permit a maximum password length of at least 64 characters.
Verifiers and CSPs SHOULD accept all printing ASCII [RFC20] characters and the space character in passwords.
Verifiers and CSPs SHOULD accept Unicode [ISO/ISC 10646] characters in passwords. Each Unicode code point SHALL be counted as a single character when evaluating password length.
Verifiers and CSPs SHALL NOT impose other composition rules (e.g., requiring mixtures of different character types) for passwords.
Verifiers and CSPs SHALL NOT require users to change passwords periodically. However, verifiers SHALL force a change if there is evidence of compromise of the authenticator.
Verifiers and CSPs SHALL NOT permit the subscriber to store a hint that is accessible to an unauthenticated claimant.
Verifiers and CSPs SHALL NOT prompt subscribers to use knowledge-based authentication (KBA) (e.g., “What was the name of your first pet?”) or security questions when choosing passwords.
Verifiers SHALL verify the entire submitted password (i.e., not truncate it).
In a simple language?
Your password should be 15 characters (min 8 and max 64)
You can use any keyboard character or even emojis as your passwords
You will not be forced to use complex passwords
You will not be forced to change passwords unless they are compromised
You will not store any hints to the password in an unauthenticated manner
You will not have ‘security questions’ - mother’s maiden name and first cat’s wife’s name, etc.
Your entire password will be verified.
In addition to this, there are certain other helpful things that might ease the work of the password owner:
Implementing blocklists (blocking most commonly used, vulnerable passwords)
Providing helpful hints to choosing a strong password.
Rate limiting (only certain number of password attempts allowed)
Allowing the use of password managers (for those pesky sites that do not allow copy-paste of a password)
Then, the document goes on to talk about all the other types of authenticators. For example, there are guidelines for single factor OTPs (when OTP is the only means of authentication) and different ones for multi-factor OTPs. There are guidelines on the use of authenticators and guidelines on how not to bind users to authenticators of a particular type.
In short, this document is full of useful guidance and not just a new password guideline.
NIST SP 800-63C - Federated Identity and Assertion
This is about federated identify management (when you outsource your identity management). Read this in case you are a federated identify service provider.
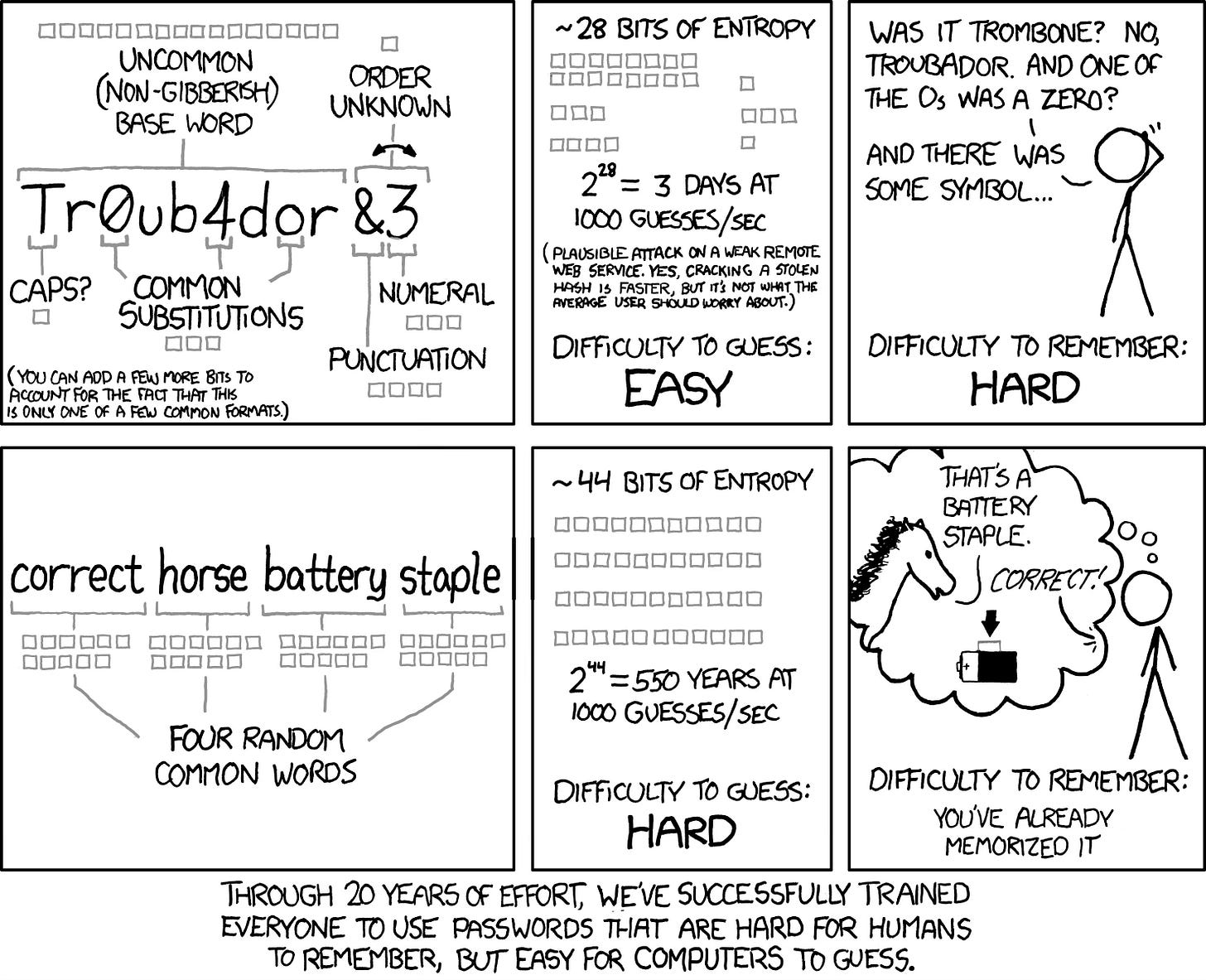
What’s with the cartoon then?
Well, the XKCD cartoon that you see was released in 2011. It highlights a concept called ‘information entropy’ and argues that passwords should be longer but memorable and they would still be more secure than the complex passwords with many restrictions.
It took 13 years for the truth of the cartoon to come up as an NIST guideline :).
The title of my first book, released in 2022, “Monkey Shakespeare Typewriter: Cybersecurity for Everyone” is based on this concept for creating a secure password. It’s gratifying to see this concept validated by NIST.
Take Action:
First, update your password policy. Please.
Send this out to all your app developers. This madness of complex passwords must stop. Just use 15 character passphrases.
Use this as a tool to get a budget for a corporate password manager, if you don’t already have one.
Count your blessings, because users are cursing you less now.
In this battle of security vs. usability, the balance wins. Long passwords are not a problem, as long as they they are easy to memorise. Muscle memory builds up over time, so changing passwords often is not a good idea.