Lawsuit against CrowdStrike | A risk assessment manifesto (finally)
#164 - The 'Crowdstruck aftermath | The key principles to conduct a risk assessment
Delta files a $ 500 million lawsuit against CrowdStrike
‘Cut corners and circumvented testing’, says the lawsuit
Your cybersecurity Karma comes back to haunt you
If you have been living under a cybersecurity rock and did not know about the global blue screening caused by an innocuous CrowdStrike upgrade, read my post here:
The sequel to the story is going to be a courtroom drama. Delta Air Lines, filed a US$ 500 million lawsuit against CrowdStrike for causing a loss to their business.
Delta alleges that CrowdStrike was grossly negligent and that they breached contract.

The lawsuit is available on this website. It makes for an excellent read. CrowdStrike has responded that Delta is trying to hide their outdated tech stack by blaming CrowdStrike.
Take Action:
For Cyber Insurers
This should be a case of phenomenal interest. Will Delta’s cyber insurance pay for the outage? Will CrowdStrike’s cyber insurance pay for the liability? It’s more likely that the Errors and Omissions policies will come into play. Follow the case
Does your underwriting consider supply chain risks? How do you determine a risky supply chain? How do you determine your insured’s liability in case of a tech supply chain disruption?
For cybersecurity professionals
Have you considered the outage of the ‘deep tech’ in your risk assessments? Deep Tech is tech so embedded in your infrastructure, that you do not even recognize that it exists
How do you deal with risks that are very low probability, but really high impact - like CrowdStrike? Or a Google workspace, Okta, Azure AD outage? Do you build resilience? Do you accept the risk? Think about your low probability (frequency) - high impact (severity) risks before they turn into a $ 50 million lawsuit!
How do you conduct a risk assessment?
By following simple, universally accepted principles
Last week, I spoke about us, cyber professionals, not knowing what we mean by a risk. You can read it here:
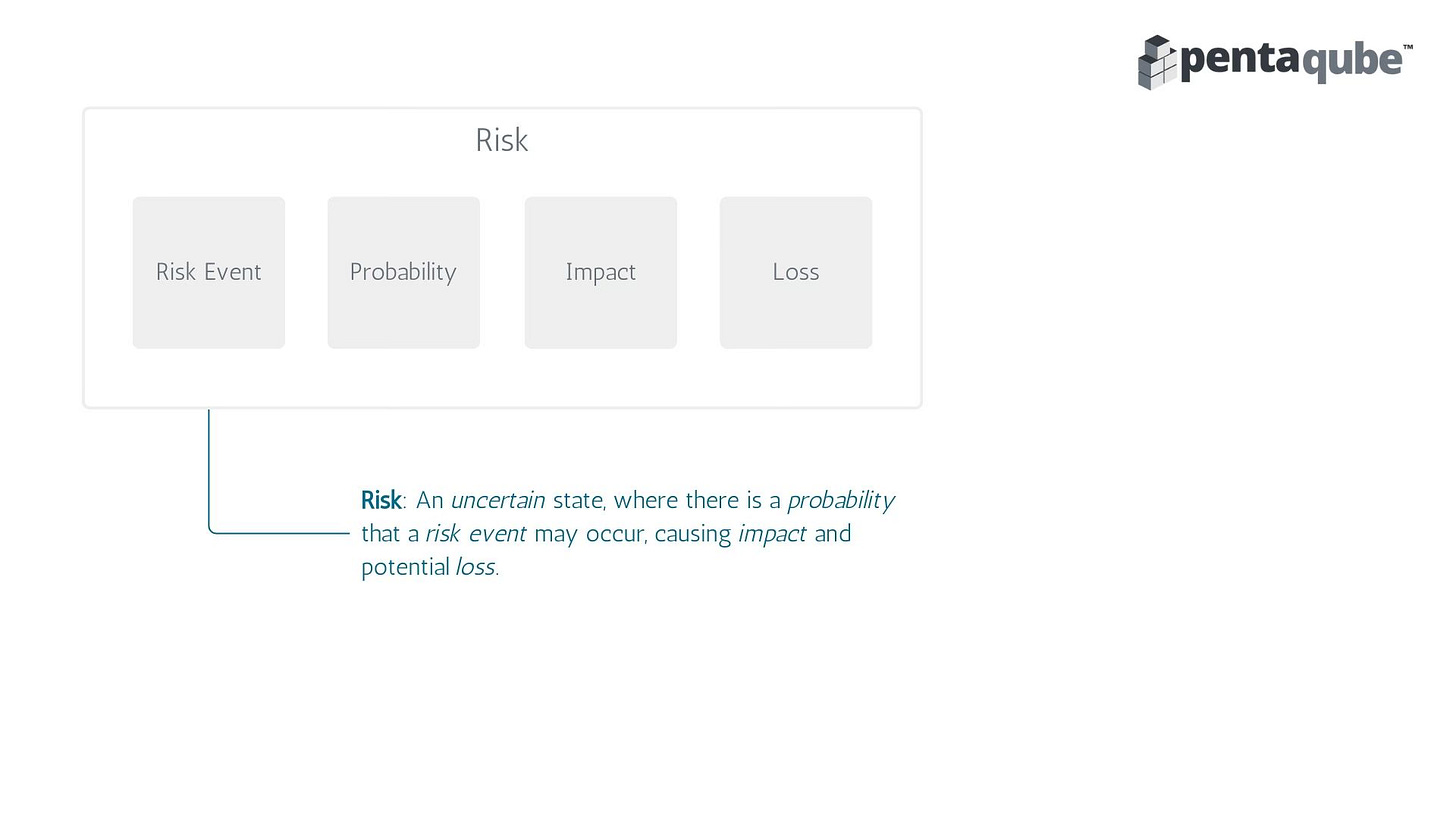
Rather than sit back and wallow about the problems of cyber risk professionals, we decided to take matters in our own hands and define risks. Here is a basic definition. I will be posting a more detailed note on how this definition differs from all the other definitions floating around.
The key here is the term ‘Risk Event’ - will release a definition soon.
There are various methods for conducting risk assessments. Each one is followed almost like a religion. The quantifiers pooh-pooh the qualitative assessors. The qualitative assessors allege that quantification is an eyewash and finally it’s just gut feel put into numbers. Some swear by ‘threat-vulnerability-risk’ pairs and get very upset if a threat is represented as a vulnerability and vice versa. Others say ‘ a risk is a risk’.
We realised that having a set of guiding principles, a manifesto, for conducting risk assessments would be valuable. So, we set out building them. We released them for everyone to use. We have a project on GitHub for it. Follow it if you want to know the updates.
An easy to read website for the principles is here. Feel free to review, change, update and use these principles in designing your risk methodologies. Please feel free to ask questions and debate the manifesto.
Take Action:
It is about time that we cyber professionals have a risk assessment manifesto. This is the start.
Review your risk assessment methodologies against these principles. Identify if your methodology requires a change, or if the principles should be updated.
Engage with your peer group and start discussions.